A Journey to the Firmware of ZTE H267A: Part I
The Story
A couple of months ago, I wanted to replace my ISP provided ZTE H267A router with Ubiquiti USG. I already knew from my past experiences that it would be easy to configure internet connection but, what I did not know was configuring IPTV alongside with internet connection is a hell of a thing.
The problem here was the missing knowledge on my side. I did know my ISP username and password, but I had no clue about what are the configurations used for the IPTV part. Either I needed to find the configuration, or find the firmware and its root password.
I tried too many things and failed too many times, but after a couple of days, I decided to leave the ISP’s router as it is.
Recently, I found a bit of free time and reconsidered to try that again. Fortunately, after a couple of hours of research, I found a blog post series that explains how to find firmware of the same ISP’s different router (Huawei HG253S).
I read all of those fluently written blog posts in one sitting, and I immediately started to prepare my environment without a second thought.
So, here I am writing a similar post for ZTE H267A after successfully obtained what I need in the first place.
Analysis
The first thing I did was to check if my router is doing the same thing to get its configuration.
I began by checking the open ports of the router:
|
|
As we can see from the result, there is no open port for SSH or Telnet. Even if we could find the ports we need open, we couldn’t use it because there is no password we know for this specific router.
To reveal which URL our router uses to fetch its configuration, we need to capture the packets going through the wire between the router and the ISP. To do that, we need 2 ethernet interfaces, one connected to the ISP, and the other connected to the router.
After connecting ethernet cables, I created the bridge interface using the following commands:
|
|
I opened up Wireshark and started capturing on br0 interface and reset the router to its factory settings.
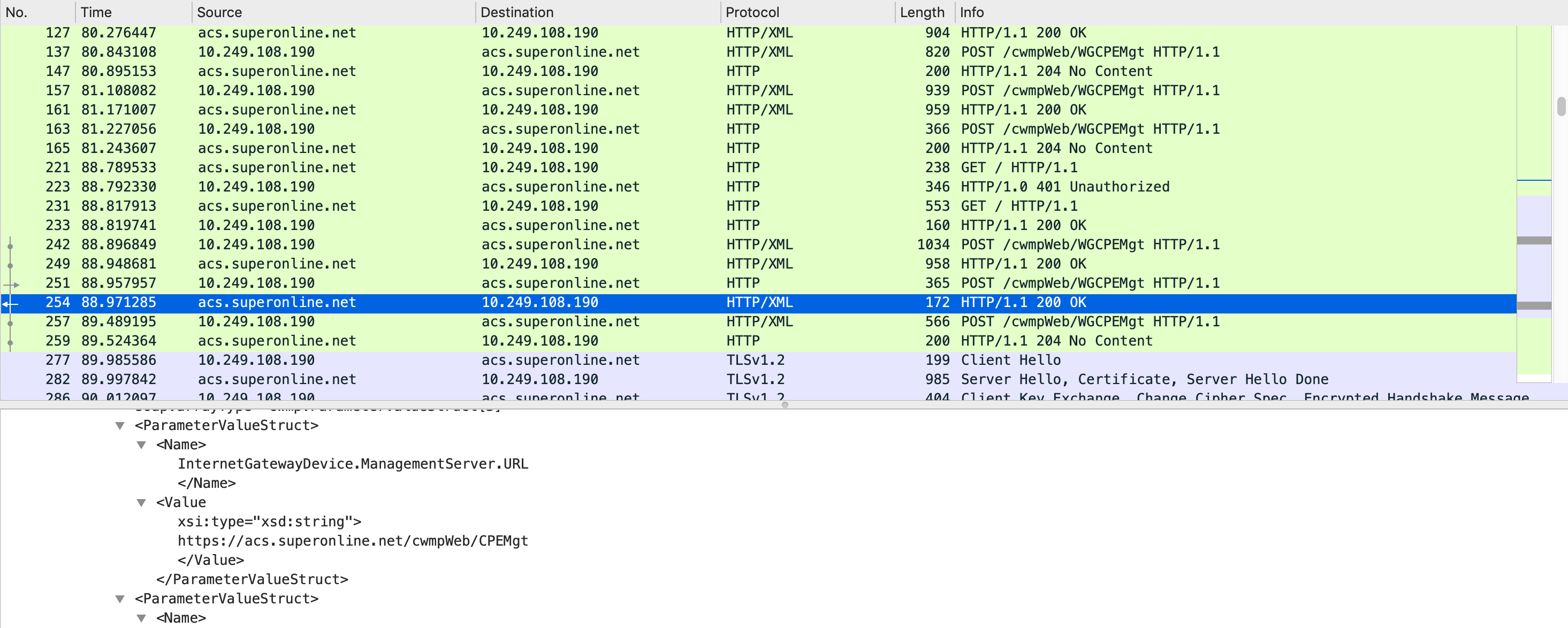
There are 3 things we can understand from this capturing.
- Initial communication is using
http://acs.superonline.net:8015/cwmpWeb/WGCPEMgt. - At some point, ISP sends the configuration server URL with
InternetGatewayDevice.ManagementServer.URLkey andhttps://acs.superonline.net/cwmpWeb/CPEMgtvalue. - After receiving the configuration URL, the router starts TLS connection with the configuration server over
https://acs.superonline.net/cwmpWeb/CPEMgtURL and443port.
I had all of the information to prove that my router has the same config as mentioned in this blog post series. So I could set up my environment to move forward, and finally, I would be able to find my router’s password.